MicroStrategy ONE
Integrate MicroStrategy Library with Microsoft Intune MAM Functions in iOS
You can use the Intune portal to add an extra layer of security to iPhones and iPads that are running MicroStrategy Library.
For Intune SDK users:
- It’s not necessary to enroll your device with Intune Comp Portal. It is possible to run the app on an iOS simulator or new device without enrolling the device.
- The Intune App SDK can use MSAL to perform authentication and enroll the application to do MAM. This includes getting and applying app configuration settings and app protection policy settings.
Microsoft Authentication Library (MSAL) is used to support authentication, conditional launch, and register the user identity with the MAM service for management in deployment and installation.
Your organization must be enrolled in the iOS Developer Enterprise Program. For information about this program, visit the iOS Developer web site.
See What's new in the Mobile SDK for iOS for the Xcode and Apple iOS SDK versions you need to use to develop and compile your application. Previous versions can be downloaded from the Apple Download site.
You must create a wildcard App ID for your application, using the iOS Provisioning Portal. A wildcard App ID is of the form [BundleSeedID].*, where:
- BundleSeedID is an alphanumeric code that is generated by Apple when you create the App ID.
- The asterisk (*) is a placeholder for the Bundle Identifier of the App ID. The Bundle Identifier is used by iOS to identify the application on your device. You set the value of the Bundle Identifier property in the property list file of your Xcode project. Replace the value of the asterisk (*) with an appropriate string using reverse-DNS format and com.yourCompanyName.YourAppName. For example, we use the default value of com.microstrategy.iPad for an iPad app or com.microstrategy.MSTRMobile for an iPhone app to integrate with Intune.
Intune allows customers to upload their mobile applications via their Intune Console or select apps directly from the Apple App Store. There is no need to set up a local app or web server.
Configuration and App Deployment on the Intune Console
Register the Application in Intune Console
- Add an application in Home > Azure Active Directory > App registrations > New Registration, provide the app name, choose Multienant type, and click Register.
- In Overview, copy the Application (client) ID as the value of ADALClientId in IntuneMAMSettings in Info.plist, to perform authentication with MSAL.
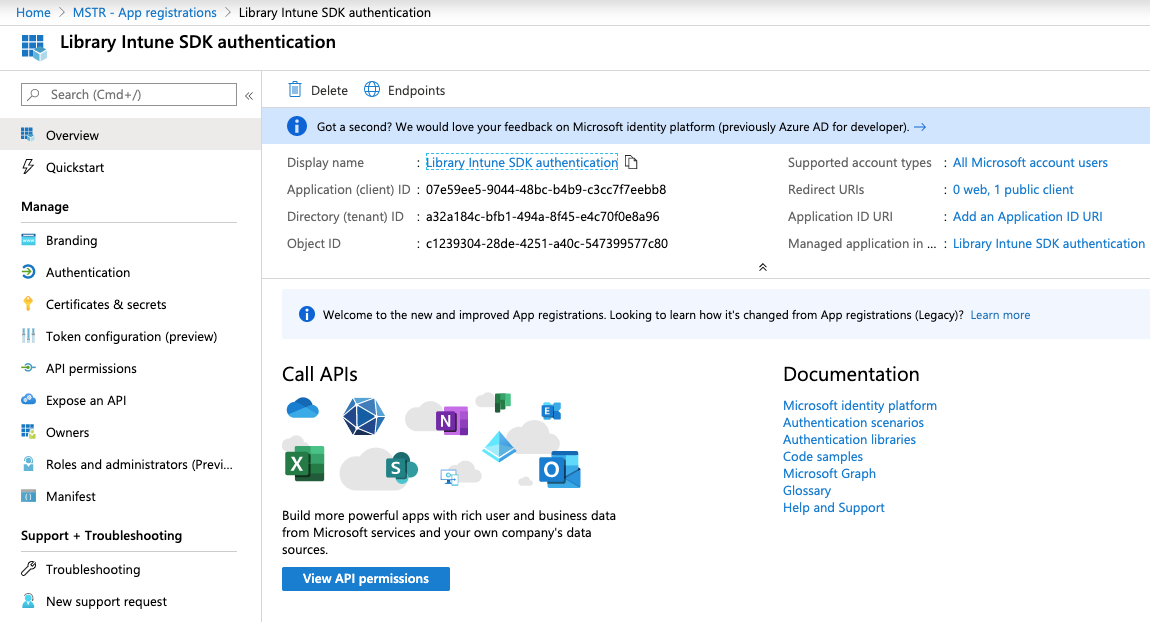
Configure iOS/macOS Authentication
- Under Manage, click Authentication, click Add a platform, and choose iOS/macOS > input Bundle ID > Configure.
- Copy the Redirect URI as the value of ADALRedirectUri in the IntuneMAMSettings of the project Info.plist in Xcode.
Add API Permissions
-
Choose API permissions > add a permission > APIs my organization uses > choose the app.
- Select DeviceManangementManagerdApps.
- Click add permissions. For more information about adding API permissions, see Give your app access to the Intune app protection service.
Upload the App and Create an App Protection Policy
Create an .ipa file with Xcode:
- Add an App protection policy in Home > Microsoft Intune > Client apps > App protection policies. Assign it to the app you uploaded.
- You can also define the app restrictions in the policy. For more information, see iOS app protection policy settings.
- You can also control the app's behavior via AppConfig in Home > Microsoft Intune > Client apps > App configuration policies. For example, you can define the configuration URL. To get the configuration URL, see Library Administration Control Panel.
After you make changes to the app protection or configuration policies, it takes approximately 15 minutes to an hour for a device's app to receive the updated policy.
Now you can test and verify your new Intune Integrated Library app! It is recommended that you set up a security PIN when launching the application.
How to Use Intune AppConfig with Intune Integrated iOS Library SDK
Starting in MicroStrategy ONE Update 11 November monthly release, MAM AppConfig for Intune integration with iOS Library SDK is supported.
In the Microsoft Intune Admin Console, two types of policies govern the behavior of Intune integrated applications, App Protections Policies and App Configuration Policies.
The Intune integrated app is a fusion of the Intune SDK and MicroStrategy Library Mobile SDK. The Intune SDK is governed by the App Protection Policy and the MicroStrategy Library Mobile SDK is managed by the App Configuration Policy. You can use the following instructions to leverage the Intune App Configuration Policy to control and customize the features in the MicroStrategy Library Mobile SDK.
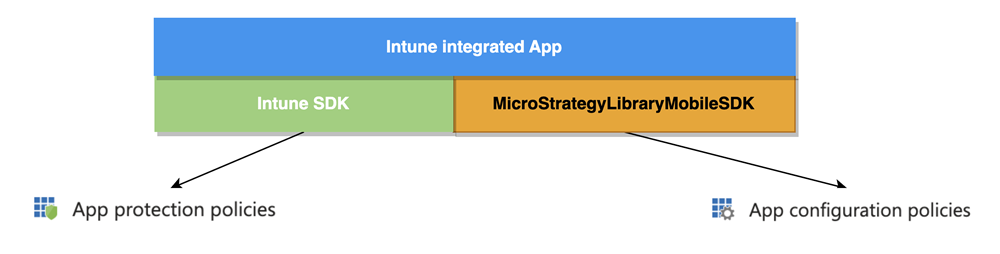
How MicroStrategy Uses MAM AppConfig
MicroStrategy establishes key-value pairs in the Mobile Application Management (MAM) AppConfig policy and utilizes the Intune SDK API to retrieve them.
Intune MAM AppConfig exclusively supports string types. MicroStrategy employs "1" for true and "0" for false.
MicroStrategy maps the key value pairs to corresponding features in the MicroStrategy Library Mobile SDK.
If EnableDataLossPrevention is set to true, all other options, besides DisableAdvancedSettings and DisablePreferences, are influenced by this configuration.
See the following mappings:
|
MAM AppConfig Keys |
MicroStrategy Library Mobile SDK Feature Keys |
Functionalities |
|---|---|---|
| ConfigurationURL | N/A | The URL to apply the first time your app launches. |
| EnableDataLossPrevention | MSTRFeatureDisablePreventDataLeakage |
The main switch for all of the app restrictions. Other options, such as DisableEmail or DisableCopyPaste, only take effect when EnableDataLossPrevention is set to "true". |
| DisableEmail | MSTRFeatureEmail | Font size in DP units. Only effective when the value is greater than zero. |
|
DisableOpenIn |
MSTRFeatureDocumentInteraction |
Features such as sharing and exporting are controlled by this option. |
| DisableCopyPaste | MSTRFeatureCopyPaste | Disable copy and paste options on all text fields and text boxes. |
|
DisableCameraAccess |
MSTRFeatureCameraAccess |
Features such as taking image and scanning barcode, are controlled by this option. |
| DisableSaveToPhotos | MSTRFeatureSaveToPhotos | Features such as saving image are controlled by this option. |
|
DisablePrint |
MSTRFeaturePrint |
Features such as printing are controlled by this option. |
| DisableLocationServices | MSTRFeatureLocationServices | Features such as location services are controlled by this option. |
|
DisableAdvancedSettings |
N/A |
Control whether to show AdvancedSettings in the Library Settings page. |
| DisablePreferences | N/A | Control whether to show Preferences in the Library Settings page. |
How to Configure MAM AppConfig
- In Intune admin center, click Home > Apps > App configuration policies.
- Click Add and choose Managed apps.
- Enter the policy name and choose the app that you want to apply your policy to.
- Click Next.
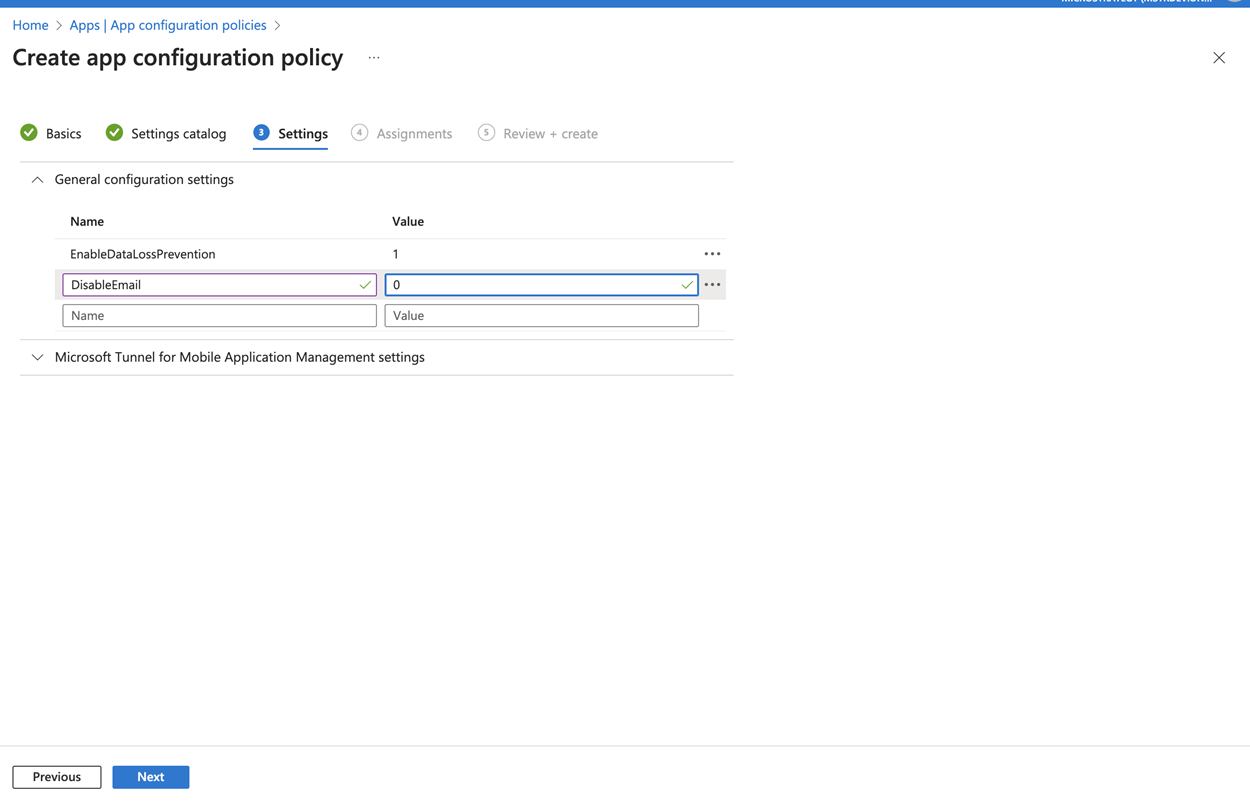
- In General configuration settings, enter the key value pairs that you need to control the MicroStrategy Library Mobile SDK.
- Click Next to configure other settings and assign users or groups.
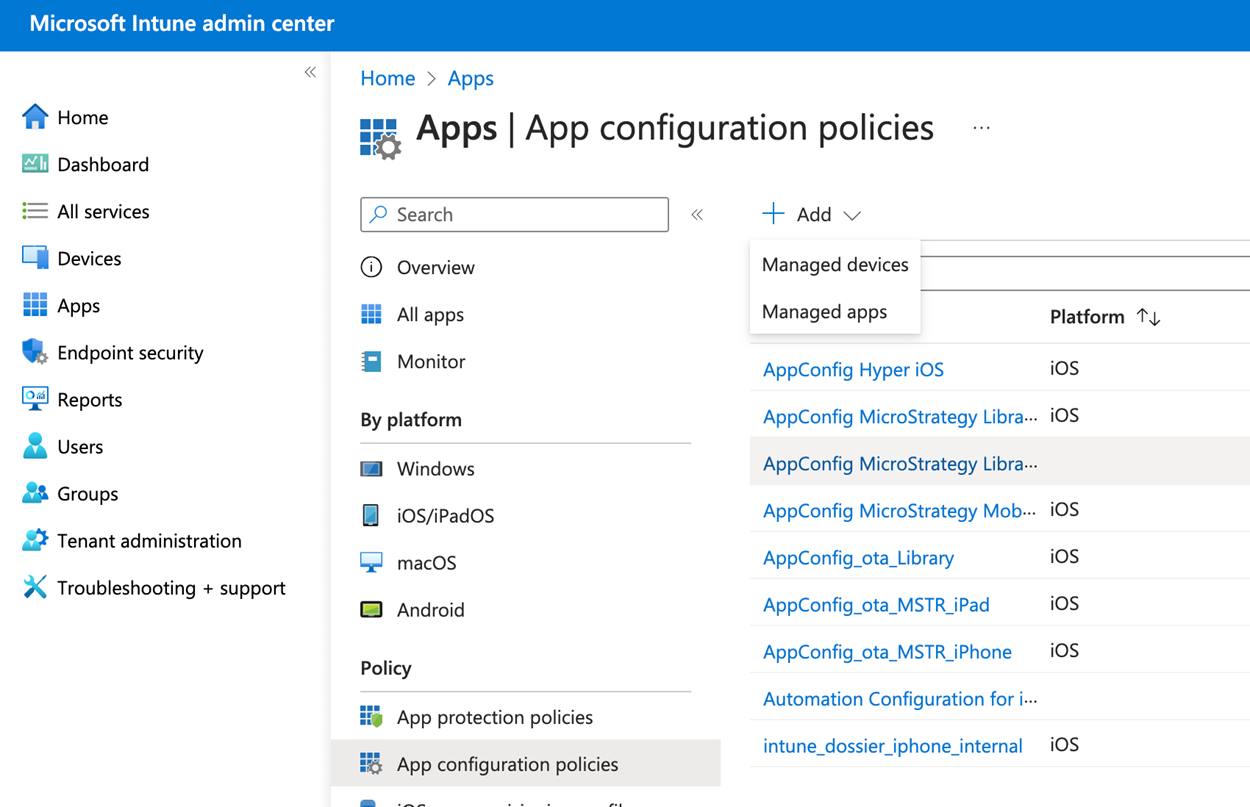
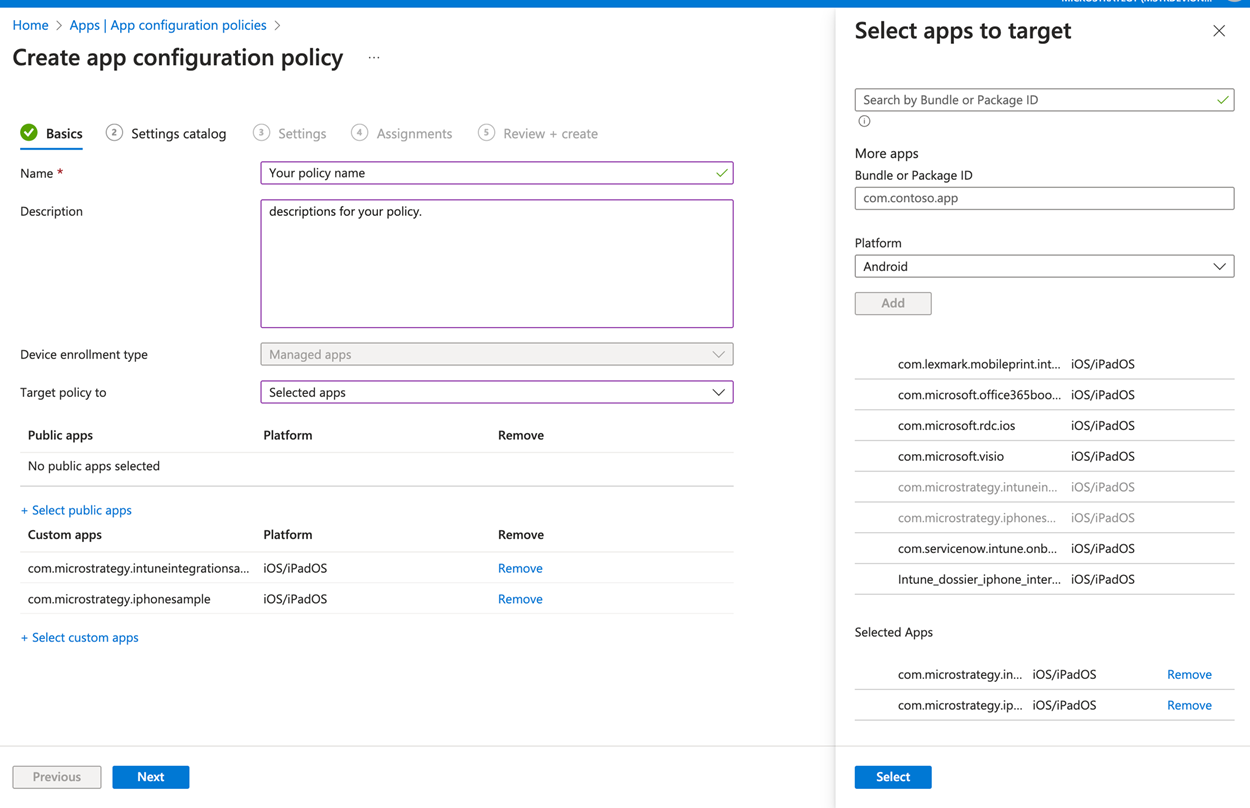
You can't choose the value type in Intune MAM AppConfig so you need to use the string value to represent the boolean value. For true, enter "1" and for false, enter "0".