MicroStrategy ONE
Integrate with AppConfig-Compliant EMM Providers in Android
AppConfig delivers the first standard approach to configuring and securing apps in the enterprise by defining a collection of best practices for enterprise application developers to interpret app configurations and security policies from EMM (Enterprise Mobility Management) systems, and for EMM systems to configure and secure mobile applications. These best practices make it simpler for developers to implement a consistent set of controls so that enterprise IT administrators can easily configure and manage apps from any participating EMM platform. AppConfig lets enterprises leverage their existing investments in EMM systems, VPNs, and identity management solutions.
MicroStrategy Mobile is designed to take advantage of the configuration and security capabilities provided by AppConfig. For Android devices, AppConfig uses a feature called "App Restrictions" to build on the extensive app security and configuration frameworks available natively. EMM providers can send configurations (app and security) from the admin server to managed devices via the "Restrictions".
Many applications require users to enter URL, port, email address, and various configurations as part of a one time setup of an application. By leveraging native APIs, AppConfig lets administrators use the EMM server to set these configurations remotely. This simplifies the setup process for end users and alleviates the help desk and documentation burden caused by manual setup. App developers define a set of configuration keys the app accepts from an EMM server and administrators simply set the keys and values in the EMM provider’s management console and they are pushed to the app.
Getting started
Before you begin your integration, make sure you have met the requirements and compiled your MicroStrategy Mobile app. Once you have done this, you are ready to push configurations, per app VPN settings, and security restrictions to the MicroStrategy Mobile app.
To use MicroStrategy Mobile for Android with an EMM provider that supports the AppConfig protocol, you must first meet the following prerequisites:
- You must have an operational EMM system, such as AirWatch. The instructions in this topic use AirWatch as the example. Refer to the documentation provided by your EMM provider for a detailed explanation of how to perform the tasks described in these instructions in your environment.
-
AirWatch must be integrated with Android for Work .
-
The AirWatch console must be registered with a managed service account on Google Play for Work and be configured as your EMM provider.
-
Devices must be enrolled with AirWatch with a work profile and have encryption enabled.
-
The app must be added for the enterprise on Google Play for Work and registered as a public app on the AirWatch Console.
-
If you want to customize MicroStrategy Mobile for Android, you must install the Android development environment and set up the MicroStrategy Mobile project.
It is recommended that you use Android Studio. Consult your Android documentation to ensure that your system meets the Android Studio requirements. To set up the Android development environment, download Android Studio and confirm the following:
- The Android SDK path is correct
- You installed the Android SDK version mentioned in What's New in the Mobile SDK for Android
- You installed JDK 7 or higher
A detailed explanation of how to set up Android for Work in your environment is provided below:
-
Register Android for Work
Android for Work is a program developed by Google which provides enterprise level data separation and security for Android apps. Android for Work is required for the main AppConfig features such as app configuration and app security. Integrating the AirWatch console with Android for Work consists of the two step listed below. Consult your AirWatch documentation for detailed instructions on how to register.
-
Create a Google Service Account using the Google Developer Console The Google Service Account is a special Google account that is used by applications to access Google APIs and is required to set up Android for Work for your enterprise.
-
Configure Android for Work Setup.
After the configuration is done, go to the settings page at Groups & Settings > All Settings > Devices & Users > Android > Android For Work on the AirWatch console. If you click the Test Connection button, it should show a "Service Account Setup Successful" message.
-
-
Enroll the device
To interact with the AirWatch console and Android for Work, the device must be enrolled with a work profile and have encryption enabled.
-
To enroll a device, download AirWatch Agent from the Google Play Store and install it on your device. Use the Server URL, Group ID and Username you receive in the email to enroll your device.
- To support Android for Work, the device must be encrypted. You can choose to encrypt the device during the enrollment process, or manually encrypt the device in Settings > Security before enrollment. The encryption usually takes about 30 - 60 minutes, and requires 80% or above battery level. During enrollment, the Agent will ask you to provide a SSO password.
After enrollment is completed, the apps managed by Android for Work are covered by a red briefcase icon. These apps are referred to as badged apps, and are shown in a unified launcher with the user's personal apps.
-
-
Create the Android for Work profile
You must create an Android for Work profile to ensure proper usage of devices and protection of sensitive data. On the AirWatch console, you can create the profile in Devices > Profiles > List View > Add > Add Profile. Select "Android" as the platform type and "Android for Work" as the configuration type. Please note that this profile is different from the normal Android device profiles.
-
Add applications to AirWatch
Internal apps are company-specific apps developed by your organization that you may not necessarily want to be searchable in the public app store, but you want your users to have access to this application from their device. You still add these apps to Google Play for Work so that they are available to Android for Work specific users.
You upload your application by logging into the Google Play Developer Console with your enterprise credentials. There is an additional option to enable, Restrict Distribution, which only allows users of your domain to view this application on Google Play for Work (the badged app play store). Once you've added your internal application to the developer console, these apps are treated as public applications.
Since the MicroStrategy Mobile app for Android is already available on Google Play, you simply need to approve the app so it can be uploaded to the AirWatch Admin Console.
-
Navigate to Google Play for Work.
-
Login to the site using your Enterprise account for Google Play for Work.
-
Search for MicroStrategy Mobile and select the Approve option.
-
View the permissions for the applications and follow the prompts to confirm approval.
After the application is approved for the enterprise, you can upload it to the AirWatch console and make it available in the App Catalog:
- Navigate to Apps & Books > Applications > List View > Public in the AirWatch console and select Add Application.
- Select the Android Platform.
- Select Import fromPlay to retrieve a list of approved applications to add to the console.
- Select Next and choose the desired applications for Import.
-
Configure and Secure MicroStrategy Mobile
Once you have met the prerequisites, you are ready to use AirWatch's "App Restrictions" to distribute MicroStrategy Mobile configuration information to all your managed devices, enforce security policies and access control, and enable MicroStrategy Mobile to use an App tunnel to connect to back end and corporate networks.
To publish MicroStrategy Mobile:
- Open the AirWatch Console, upload MicroStrategy Mobile, and click Save & Assign to assign the app to devices.
- On the Add Assignment screen, select the device group that has the devices that MicroStrategy Mobile will be pushed to and set the delivery time to control when it will be delivered.
- Edit the assignment to set up the application configurations, including the configuration URL and application security restrictions, and the per-app VPN profile (for the AppTunnel). Navigate to Apps & Books > Applications > List View. Click the Public tab, select the MicroStrategy Mobile app and click the Edit or Edit Assignment icon. Select the Deployment tab and the Deployment page opens. You use the Deployment page and other settings on the AirWatch Console to configure the following:
With AppConfig, a mobile administrator can define a set of configuration keys that the MicroStrategy Mobile app will accept from the EMM server. These configuration keys are defined in the EMM administration console, normally stored as part of a profile assigned to the app for deployment. You can set up these configurations on the AirWatch console during the process of application distribution. The EMM provider also has the ability to update the configurations over the air at any point in the future to an existing application, without requiring the app itself to be reinstalled. You can create different profile assignments to deploy the application to different groups of devices, thereby applying different configuration settings to each.
Security Policies and Access Control
Organizations require granular security and data loss protection within their enterprise applications to prevent sensitive data and documents from leaking outside company control. For example, an app may include functionality that an enterprise wants to disable for security reasons, such as the ability to synchronize data with a public cloud like file storage services. AppConfig leverages the out-of-the-box capabilities that Android provides to enforce security settings and access control on enterprise apps. Some security capabilities are natively provided by the operating system and the EMM vendor, while other capabilities require the implementation of an app configuration.
An application may require access to web services residing behind a corporate firewall, which requires secure app tunnel. A common use case for cloud-based apps is the ability to federate authentication to an organization's identity provider (IDP). Secure app tunneling should only allow certain applications restricted access to certain intranet endpoints. The per-app VPN protocol in Android achieves the goal of a secure App Tunnel, as long as the app is managed by an EMM such as AirWatch. AirWatch distributes the VPN profiles to its managed devices and let the apps use the profiles to set up their own VPN.
You configure many of these settings on the Deployment page shown below:
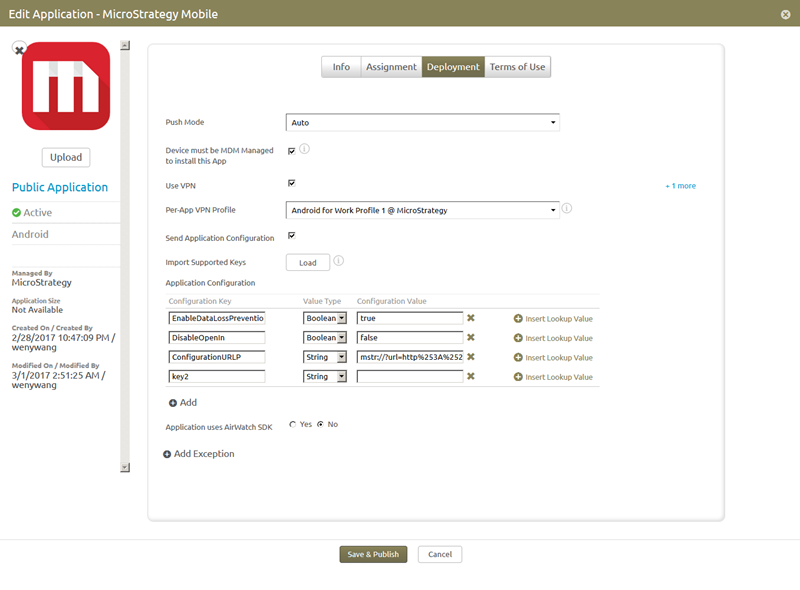
App Configuration
Under Application Configuration on the Deployment page, set the value of ConfigurationURL which is a link to a full set of configuration settings such as Intelligence Server and Mobile Server connectivity, project information, home screen configuration, and general app settings. You can initialize the application by putting the configuration URL into Application Restrictions. The configuration URL is a key-value pair. To distinguish configuration URLs between Android phone and tablet, use the following keys for the URL:
- ConfigurationURLP: for Android phone
- ConfigurationURLT: for Android tablet
Set the value of the configuration URL key to the URL that has the configuration information. The URL must be a String value whose "%" encoding characters have been replaced with "%25". The ConfigurationURL can be obtained from the MicroStrategy Mobile Administrator page, under Mobile Configurations. For information on how to create a mobile configuration, refer to Configuring connectivity settings for iOS and Android devices.
Before the configuration URL is applied, the user is asked to confirm whether he/she wants to reconfigure your application. If the user selects "No", he/she will be prompted again the next time the application is launched.
Security policies and access control
Some security capabilities are natively provided by the operating system and the EMM vendor, while other capabilities require the implementation of an app configuration.
The following security capabilities do not require configuration on the AirWatch Console:
- Encryption
EMM vendors can enforce Android encryption for enterprise apps. When you enroll the device using Android for Work, the device is automatically encrypted as part of the enrollment process . - Prevent App Backup
Apps deployed under Android for Work / Android 5.0+ managed profiles will not participate in any backup infrastructure. - Passcode
EMM vendors can enforce “data protection” for enterprise apps by applying a passcode policy on the device. The passcode should be app specific. For MicroStrategy Mobile, this is accomplished by enabling Device Policy Control (DPC) in the admin cofiguration and enforcing the passcode only for Work Profile managed applications.
To set the following security policies, you use the Deployment page and other settings on the AirWatch Console.
-
Custom Security Settings
On the Deployment page, administrators can restrict the availability of some app features for the purpose of preventing data leakage or data loss. The administrator can send custom security settings to MicroStrategy Mobile via Restrictions during the process of application assignment on the AirWatch console. The administrator can also update the configurations for an existing AppConfig application over the air at any point in the future, without requiring the application itself to be re-installed.
The following restrictions can be added as BOOLEAN key-value pairs:
-
EnableDataLossPrevention
-
DisableEmail
-
DisableOpenIn
-
DisablePrint
-
DisableCopyPaste
-
DisableCameraAccess
-
DisableLocationServices
-
DisableSaveToPhotos
The EnableDataLossPrevention key is the main switch for all of the app restrictions. Other options, such as DisableEmail or DisableCopyPaste, take effect only when EnableDataLossPrevention is set to "true".
To verify the security settings in MicroStrategy Mobile, go to Diagnostics > Configuration > Internal Diagnostic Setup and set the level to Messages. When you view the log, you can see the security settings.
-
Managed "Open In" is a device-specific access control feature that is applied across all applications. EMM providers are enabled directly by Android to separate and provide a strong boundary between personal and corporate apps. Neither personal nor corporate apps can directly access data (read or write) in the other space on the device. MicroStrategy Mobile uses an Android for Work / Android 5.0+ managed profile to enforce the policy of having files open only in managed applications. The apps uses Content URIs and not File URIs for both functional and security reasons.
To enable the Managed “Open In” capability in AirWatch:
-
Go to Devices > Profiles > List View > Android > Android for Work > Restrictions > Configure > WORK AND PERSONAL.
-
Select or deselect the following configuration items:
- Allow work apps to access documents from personal apps
- Allow personal apps to access documents from work apps
- Allow personal apps to share documents with work apps
- Allow work apps to share documents with personal apps
The device profile leverages the restrictions on Android. For example, when "Allow personal apps to access documents from work apps" and "Allow work apps to share documents with personal apps" are not selected, a MicroStrategy document cannot be shared from the MicroStrategy Mobile app to personal applications. When "Allow personal apps to access documents from work apps" and "Allow work apps to share documents with personal apps" are both selected, an additional option called "PERSONAL APPS" is available. If you tap the "PERSONAL APPS" icon, the document can be shared from the MicroStrategy Mobile app to personal applications.
-
-
Use the Android for Work / Android 5.0+ managed profile to disable screenshot access on MicroStrategy Mobile. To enable the screenshot control capability in AirWatch, go to Devices > Profiles > Android > Android for Work > Restrictions > DEVICE FUNCTIONALITY and select the configuration item, "Allow screen capture". To disable the screenshot control capability, uncheck the box. Please note that this option does not affect the Annotations feature.
-
When you distribute the app to the device as a managed application in AIrWatch, admins have the ability to perform one time commands including remotely wiping devices, locking devices, and changing passcodes from the AirWatch console. To get to these commands, go to Devices > Details View > More Actions and select "Enterprise Wipe". The Android for Work Profile and Work Managed Device capabilities will be removed from the Android device.
-
Copy/Paste Control
Use the Android for Work / Android 5.0+ restrictions profile to limit copy and pasting to only managed applications. This restriction limits copy/paste clip board access to prevent cross work/personal copy/paste. To set copy/pase control in AirWatch, go to Devices > Profiles > Android > Android for Work > Restrictions > WORK AND PERSONAL and select the configuration item, "Allow Pasting clipboard between work and personal apps": If this item is not checked, then copy/paste is disabled between work and personal apps.
-
App Tunnel
To enable per-app VPN, you must:
- Create a device profile with AppProxy VPN enabled, and assign it to your device. For example, on the AirWatch console, you configure and distribute the VPN profile in Devices > Profiles > Add Profile > Android > Android for Work > VPN, where you specify the domains/hostnames in the profile to auto-trigger the VPN.
- Configure VPN in the device profile. For example, on the AirWatch console, go to VPN > Configure and set the Connection Type to "AirWatch Tunnel".
- Assuming that you have already selected MicroStrategy Mobile to in your list of public apps, on the Deployment page, select the Use VPN checkbox and choose the Per-App VP Profile to use.
- Install AirWatch Tunnel to the device and open AirWatch Tunnel. The per-app VPN only works when AirWatch Tunnel is installed on your device. You can find this app in Google Play. To make AirWatch Tunnel work, you must publish it in Google Play for Work and the AirWatch console as com.airwatch.tunnel, and then push it to the device. After AirWatch Tunnel is installed, you can manually connect to the VPNs with this public app.
- You can also find and connect to the VPNs in Settings > More networks > VPN. If you leave the device for a while when the VPN is connected, the status of the VPN sometimes becomes "Idle" in the AirWatch Tunnel app. In this case, you have to manually disconnect the VPN in Settings > More networks > VPN and connect it again.
- These settings take effect after MicroStrategy Mobile is pushed to the device. When MicroStrategy Mobile is launched, it automatically connects to the VPN server, and a key icon is shown on the left side of the status bar, indicating the VPN is activated by AirWatch Tunnel.
